Wordfence Blocks Username Harvesting
Wordfence Blocks Username Harvesting via the New REST API in WP 4.7
This entry was posted in Wordfence, WordPress Security on December 12, 2016 by mark 37 Replies
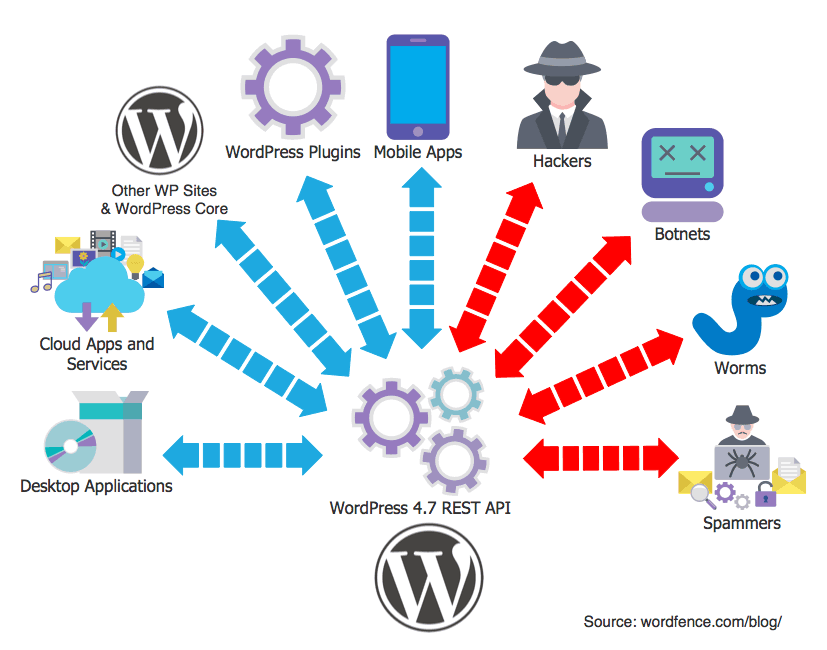
WordPress 4.7 was released 6 days ago, on December 6th. It includes a REST API that will be used by many WordPress plugins, mobile apps, desktop applications, cloud services and even WordPress core in future. Every site that upgrades to WordPress 4.7 has this API enabled by default.
The API is powerful and allows WordPress to move from being a simple web based content-management system into being an application framework. What this means is that developers can write applications that run anywhere and talk to your WordPress website. So in future you’ll be able to publish content and manage your site from the cloud, from your phone, tablet or desktop and plugin developers will be able to create new kinds of extensions that improve your WordPress experience. All of these applications will use the new WordPress REST API that was released in WordPress core version 4.7.
As the saying goes, with great power comes great responsibility. Parts of this new API are available to anyone on the internet. They don’t need to sign into your WordPress website to use the API. They can just connect and use it. With the launch of this API, we expect developers to embrace it, but we also expect hackers to find ways to exploit it.
The new WordPress REST API allows anonymous access. One of the functions that it provides is that anyone can list the users on a WordPress website without registering or having an account.
This can be exploited by bots that are launching brute-force password guessing attacks on WordPress websites. They can use this API to list the usernames of anyone who has published a post on a WordPress site. The list of users displayed via this API almost always includes a user with admin level access.
To see this WP REST API function in action, simply visit a site with WordPress 4.7 installed and hit the URL: example.com/wp-json/wp/v2/users
This will list all users that have published a post. It includes that user’s userid, username, gravatar hash and website URL. We are seeing well known brand name websites that have now upgraded to WordPress 4.7, where we are able to enumerate all usernames who have published posts, simply by visiting the above URL.
Wordfence already includes protection that makes it more challenging for bots to discover your admin username. This morning’s release updates this feature to extend this protection to the new WordPress 4.7 REST API.
Fine granularity: Keeping the bad guys out and letting the good guys in
Instead of providing an option to disable the entire REST JSON API, which some security vendors have done, we recognize how powerful and useful this new application programming interface is. We expect it to be widely embraced and to significantly enhance the power of WordPress.
To mitigate this threat, we have targeted the specific functionality in the API that exposes usernames. If you enable the feature (described below) it will simply stop anonymous users from being able to retrieve a list of users and their usernames. We don’t disable or break any JSON API functionality. Authenticated users using the API will be able to list their own user information. Authenticated users with list_users permission will be able to list all users.
We have made the REST API team aware of the new protection we have added on WordPress Slack and have received some helpful input. We will continue working with them and other developers to ensure that Wordfence enhances the security of WordPress and the new REST API, while ensuring compatibility with all applications.
How to enable protection against user enumeration
Wordfence 6.2.8 was released this morning and includes protection against attackers enumerating usernames using the new WordPress 4.7 JSON API. This option is enabled by default. To verify that this option is enabled, or to modify the setting, you can find it on your Wordfence options page with the label:
“Prevent discovery of usernames through ‘/?author=N’ scans, the oEmbed API, and the WordPress REST API”
You can find that option under the “Login Security Options” heading on the Wordfence options page.
This option is available to all Wordfence users, both free and paid.
You can find the documentation for this option on docs.wordfence.com.
We’d like to hear from you
We’d like to hear from any WP developers who are using this API and have any questions. We aren’t aware of any applications currently that rely on making unauthenticated requests to WordPress 4.7 to get a list of users. If you’re aware of any plugins or other applications that rely on the anonymous enumeration of users, and that are affected by this change, please post in our comments and we will modify our documentation.
As always I’ll be around to answer any questions from the community in our comments.
Special thanks to our team and especially Ryan Britton and Matt Rusnak for working hard to develop and test this feature in time for a Monday morning release.
Mark Maunder – Wordfence Founder/CEO.