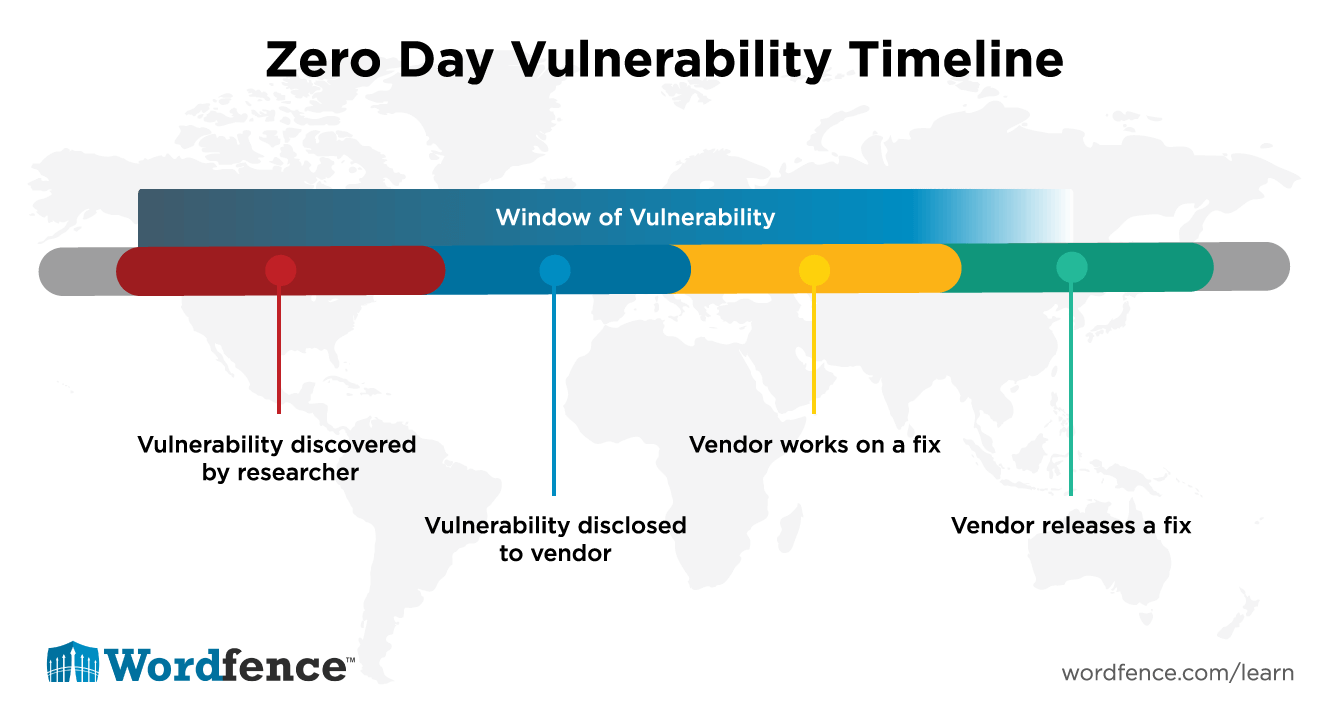
When a vulnerability does occur in a plugin or theme, there is a lag time between the vulnerability discovery and when a fix is released. We refer to this as the “window of vulnerability”. To protect yourself during this time, you need a firewall that is being actively maintained by a security team and that includes real-time updates.
The Premium version of Wordfence does exactly that. Our team works proactively to discover new attacks and to release firewall rules as soon as a new vulnerability is discovered. This protects our customers during the window of vulnerability, while the vendor works to release a fixed version of their software.
Reducing Your Attack Surface
You will also need to work to reduce the number of things that can be attacked on your website. Think of your website as a giant dartboard and a hacker is trying to throw darts that simply have to hit the board. The more plugins you run, the more themes you have installed and the more web applications you run, the bigger the surface area that the attacker can hit. Reduce your attack surface by removing unused or unnecessary applications, and you make yourself a much smaller target and your website will be much less work to maintain. You should also remove any unused accounts, especially administrator accounts, on your WordPress website.
Practicing Good Security Hygiene
Finally, you and the users of your website will need to practice good security hygiene. That means you should:
- Use strong passwords that are not easily guessable. We recommend using a password manager like 1Password.
- Enable two-factor authentication. (Wordfence Premium provides this.)
- Make sure you have reliable backups of your website.
The Basics Are Actually Not That Much Work
If you have these basic ingredients for security in place, you will be starting from a excellent base security posture. To summarize, the items I have mentioned so far are:
- Keep WordPress core updated. This happens automatically most of the time.
- Keep your plugins, themes and other web applications up to date.
- Use a firewall that is updated in real time.
- Reduce your attack surface by removing unneccesary plugins, themes, web applications and user accounts.
- Practice good security hygiene by using strong passwords, enabling two-factor authentication and ensuring your backups are reliable.
This may sound like a lot, but it really is not. Once you have configured your WordPress site with a firewall, enabled two-factor authentication, removed any applications and plugins you don’t need, and set up strong passwords, the only thing you need to do regularly is update your website plugins when needed and occasionally verify your backups. In addition to this, I would suggest keeping abreast of WordPress security trends and any ‘big’ security news. This blog consistently covers big news and important threats in the WordPress security space, so subscribe to our mailing list and you’re all set.
What About the XYZ Alternative CMS? Isn’t That More Secure?
This question comes up a lot. I think the best way to illustrate my thinking on this is with a bell curve. Imagine a curve where the X axis is how evolved a software product is and the Y axis is the number of security incidents. I’ll provide names for each evolutionary stage.
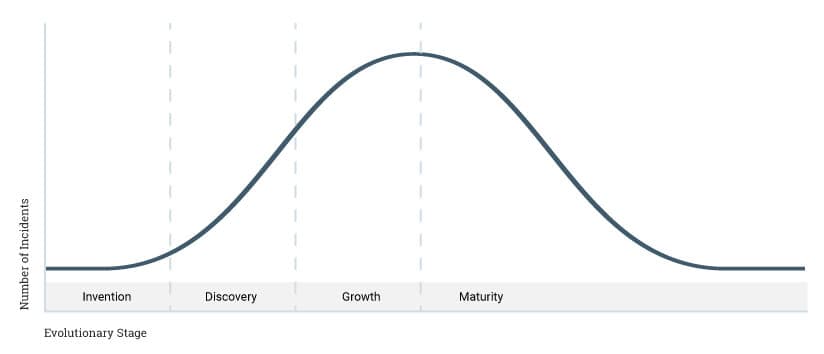
Invention
On the far left, you have a brand new CMS or other software web application that is used by the one guy that wrote the software. Hackers aren’t interested in finding vulnerabilities in this software, because it will only enable them to hack a single site. Researchers aren’t looking at the code because securing a single website won’t bring them much recognition. Vulnerabilities aren’t going to get found by hackers or researchers, and won’t get exploited. The likelihood of this very early stage software getting hacked is low.
Discovery
As the new application gains popularity, it becomes a more interesting target, because a vulnerability enables an attacker to exploit more websites. The software is early stage, so there are no security processes, teams and vendors supporting the new CMS. You can’t buy a firewall for the product. Security researchers are focused on more popular products. Hackers are beginning to discover it is a target. At this point, the number of security incidents reported in this software is rising on a steep curve.
Growth
Once the new application hits a steep growth curve, hackers begin to take a major interest. There are now enough installations out there to make it very much worth their time. The new application is still not close to the most popular CMS in terms of usage and is still not receiving much attention from researchers, volunteer teams or vendors.
During this time, the new application is extremely vulnerable. Major incidents will occur in the evolution of the software. WordPress was in this phase from about 2007 to 2013, when we saw the Timthumb hack, auto-update was not yet available and security vendors were just beginning to emerge, including Wordfence which launched in 2012. The number of security incidents during this period puts the application on the map as a target and a product worth protecting.
Maturity
As a security community develops around the application, the frequency and severity of security incidents begin to drop. A community of passionate security researchers evolves around the product. Methodologies emerge for reporting and fixing vulnerabilities securely and confidentially so that hackers never have the opportunity to exploit them.
In the WordPress universe, we still see the occasional security issue like the large scale defacement campaigns that occurred early last year when a vulnerability appeared in WordPress core. But in the Mature phase, these incidents are short and sharp because the vulnerabilities are rapidly fixed by the competent security team that has evolved around the product and with the assistance of outside researchers and vendors.
Third party security products like Wordfence are able to mitigate the impact by preventing attacks. Where incidents do occur, incident response is available in the form of site cleaning services, to ensure rapid recovery.
Where WordPress Stands
WordPress is very much in the mature phase of its security evolution, and as it continues to evolve, the number of security incidents will continue to decline and stabilize. When choosing whether you want to use a newer or alternative CMS, consider which phase of the evolution the product is and where it will be headed in the coming years.
Someone Suggested a Static Website. Isn’t That Unhackable?
An alternative approach that some are taking is to build a website that is completely static HTML and CSS with no PHP or other application components. This does not have an application that an attacker can exploit, and the website can be configured so that it doesn’t even have the ability to execute PHP, so that hackers can’t run their code.
In theory, this website is far more secure than a PHP application like WordPress. The problem is that, other than serving pictures and text, it won’t actually be able to do anything. No comments, forms, content management, e-commerce or any other application functionality. That makes this option unfeasible for most site owners.
It’s also worth pointing out that the web server itself is an application, and there have been many vulnerabilities in web servers like Apache and Nginx reported. Eliminating the application server does not make a website immune from exploitation.
Is a Cloud CMS More Secure?
For many users, a cloud CMS may never be an option because they need 100% ownership and control of their website, intellectual property and data. But if you are considering partially or fully outsourcing your website to a cloud CMS, you should keep in mind that cloud services are not immune from security breaches either.
In October 2017 we saw the cloud comment service Disqus report a major security breach which exposed the data of 17.5 million users. In February of last year we saw cloud firewall provider Cloudflare experience a breach when their systems leaked sensitive user data.
Cloud services are attractive targets for attackers because they have everyone’s eggs in their one basket. Their developers are also human and are prone to err like the rest of us. Self-hosted WordPress as a CMS platform gives you the benefit of complete control of your own security, and a community of researchers, vendors and volunteers to help you secure your site.
Are WordPress Hosting Providers Secure?
Most WordPress hosting providers do a reasonably good job of securing their customers, but occasionally we encounter a host that has what we refer to as a ‘service vulnerability’. In these cases, no matter what the site owner does to secure their own site, their site remains vulnerable due to a flaw in the hosting provider’s security posture.
Our team has developed a service vulnerability disclosure policy. When we discover a service vulnerability, our team works confidentially with the hosting provider to fix the problem. Once the issue is fixed, we publish the details. So far we have worked with four hosting companies and have successfully helped them fix their underlying security issues in all cases. We wrote about three hosting providers with service vulnerabilities in February and published details on a fourth this week.
When selecting a WordPress hosting provider, choose a provider that is reputable, responsive to fixing security issues and provides you with clear answers to any questions you may have about security.
Whether you choose WordPress as your CMS or an alternative platform, you will need to host your website somewhere. Because WordPress represents a very large and attractive market for hosting providers, the best hosts in the world have focused on providing hosting for WordPress. This gives site owners plenty of options to choose from among the largest hosting companies in the world.
A Security Researcher Said WordPress Is a ‘Security Disaster’. Is This True?
Security researchers make a living by selling security products or consulting services. They also have egos. Our industry has had a contentious relationship with vendors who make software for as long as hackers and security researchers have been around. As an industry we are working to change that. For a view into someone leading this change, check out Facebook CSO, Alex Stamos’s keynote address at BlackHat 2017.
Often vulnerability reports about WordPress core or plugin vulnerabilities are associated with hyperbole about the platform itself. WordPress is like any other application in that it occasionally has vulnerabilities. But as I discussed above, WordPress has entered a mature stage of its security evolution, and while vulnerabilities still occur, they are dealt with rapidly and in an organized and effective way.
Is WordPress Secure? That Depends on You.
WordPress can be a very secure, highly functional and well-supported platform that can serve you or your organization and scale for decades. But this requires that you follow the basic security steps I outlined above and that you stay abreast with the latest security developments.
If you run a WordPress site or are just beginning to embark on your WordPress journey, know that you have a massive community behind you, including our team, to help you secure your website for the long term. As always, I encourage you to share your WordPress security perspectives in the blog comments below.